Flatpak is not secure by default
Surely, Flatpak is safe!
Or… is it?
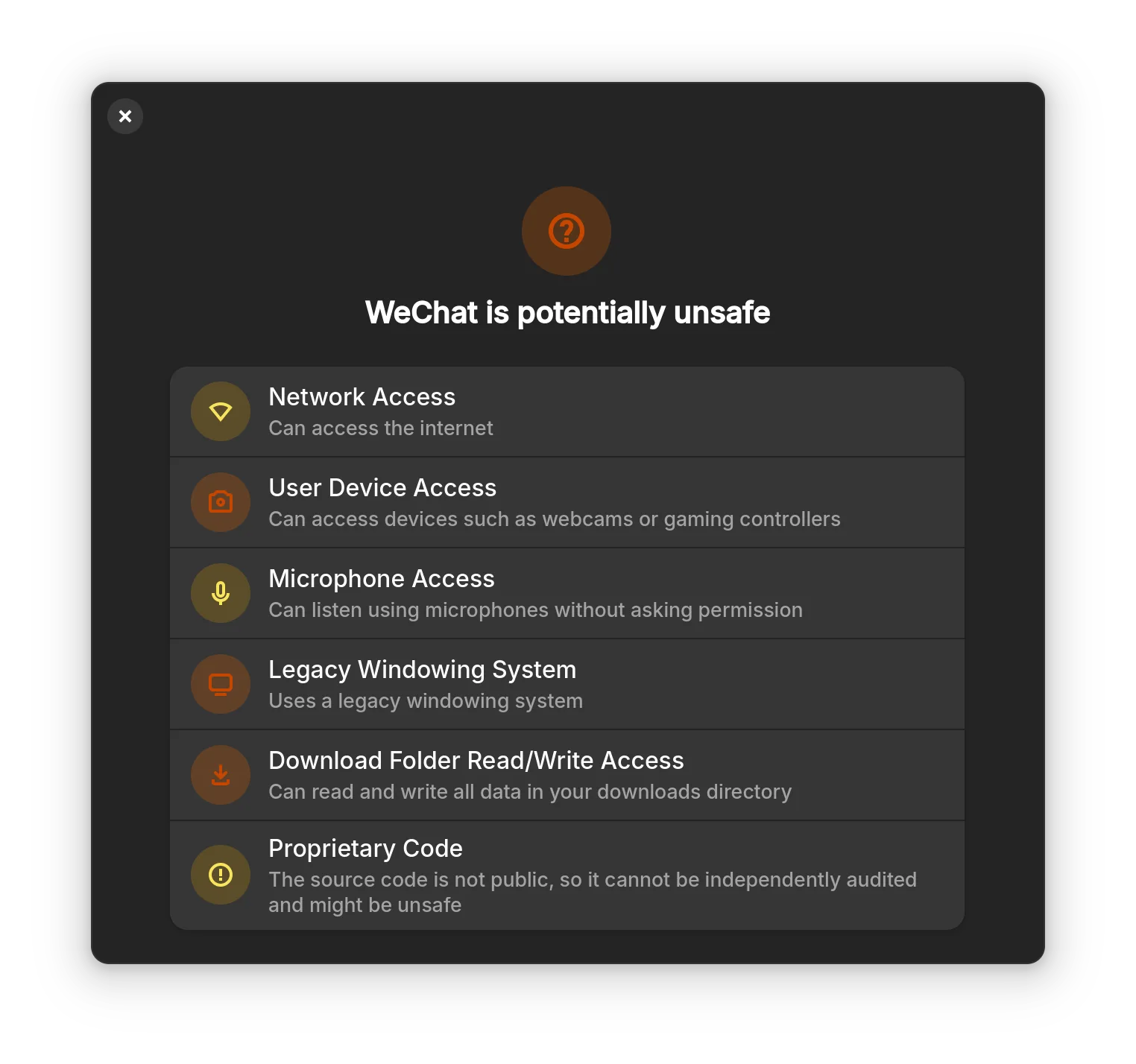
After packaging wechat-uos-qt for quite some time (that duplicated package wechat-universal-bwrap is not deleted, great AUR moderation), I decided to see how Flatpak handles sandboxing (We are looking for ways to support URL opening). As usual, you search for WeChat in GNOME Software, click install, and it should be done, right? Well, I glad there was one more thing done by me: scroll down and see this:
Whoa… Offering a proprietary app Downloads/ access? That doesn’t even make any sense. wechat-uos-qt already resolved file transfer using a Open WeChat Data action that’ll take you to the WeChat sandbox home. This isolates file and offers a convenient way to share files to whoever still using the proprietary messenger app. This seems inconsistent when compared with Flatpak Documentation:
One of Flatpak’s main goals is to increase the security of desktop systems by isolating applications from one another. This is achieved using sandboxing
While application developers have control over the sandbox permissions they wish to configure, good practice is encouraged and can be enforced.
Yes, if Flatpak does somehow enforce sandbox and good practices, then I guess allowing proprietary apps to read, write, modify your Downloads folder is a good practice. I mean, the entire permissions guideline is pretty good. That is, when these guidelines are enforced.
While the above example is a bad access rule set, see this portion of code in GPU Screen Recorder:
1 | if(geteuid() == 0) { |
1 | if(pid == -1) { |
I am no C programmer, but what these code, or should I say GPU Screen Recorder do in Flatpak, is that if CAP_SYS_ADMIN doesn’t exist, it’ll try pkexec to acquire root permission and give itself CAP_SYS_ADMIN, the new root (which, according to the manual is overloaded as hell). What you get is one more attack surface. What we know is Flatpak has serious security holes. This can probably be mitigated using bubblewrap-suid and a --cap-drop ALL (Though it opens another security hole as suid binaries are involved), but applications and Flathub itself shouldn’t accept this insecure operations by default. It is okay to provide a good out-of-the-box experience, but compromising security doesn’t line up with what Flatpak promises. This is a combination of lacking moderation and guidelines not being enforced. And it is why you shouldn’t trust bold claims.
The conclusion
Flatpak is insecure by default, and confusingly misleading. Check what permissions an app might have before launching. Running untrusted code is never safe, even in a sandbox.